Welcome to Pixalate’s Ad Fraud Series, where we highlight unique forms of invalid traffic (IVT), inclusive of “ad fraud” — across the mobile open programmatic advertising marketplace.
Here we will look at “app spoofing IVT” of apps from the Google Play Store and Apple App Store.
Key findings:
- App spoofing rates in mobile are relatively lower than on CTV, which can possibly be attributed to more difficult end-to-end implementation of app-ads.txt on CTV devices.
- Tumblr, WordScapes, and MyFitnessPal were among the biggest targets of mobile app spoofing in October.
- Gaming apps appear to be the category most targeted on iOS devices.
- Utilities appear to be the category most targeted on Android devices.
App spoofing — which is also referred to as app misrepresentation or app laundering — occurs when an app masquerades as another app. For example, an advertiser might think they are buying a spot on the Hulu app, but in truth the ad appeared on a lesser-known app. App spoofing has been central to several large-scale ad fraud schemes, including discoveries by Pixalate such as Matryoshka and Megacast.
October 2022 - Top 20 Spoofed Mobile Apps on Apple’s iOS and Google’s Android platforms
Across September and October 2022, Pixalate measured an app spoofing rate of 0.78% across all open programmatic ad impressions purportedly served on mobile devices. This is lower than what we see on CTV devices, and can which can possibly be attributed to more difficult end-to-end implementation of app-ads.txt on CTV devices. It is important to note that the 0.78% rate is based on app spoofing IVT as defined by the MRC and does not include impressions in which app spoofing and other preferential IVT types (e.g., Data-center, proxy IVT, etc.) were also involved.Below are the 20 mobile apps from the Apple and Google app stores that were most impacted by app spoofing in October 2022. App spoofing varies by region, which is why we have also broken the report down by region (North America, APAC, LATAM, EMEA). This is important because the same app might have different IVT levels in different regions. Clients can use our tools to determine the most appropriate.


Click Here to download the list with more details:

FAQs: Ad Fraud on Mobile Platforms
What is app spoofing?
App spoofing is a form of IVT in which traffic from one app is misrepresented as traffic from another. This is commonly done to make the inventory appear more valuable.
App spoofing can be generated in several ways:
- Real devices used as a botnet;
- Real devices unaware of spoofing happening in the background; or
- Artificial impressions generated by fake devices.
For a deeper dive, check out our blog on app laundering or our knowledge base.
How does Pixalate measure app spoofing?
Pixalate detects app spoofing in traffic where app identifiers (e.g., bundle ID) reported in the bid request do not match the characteristics of the app detected directly by Pixalate.
Pixalate is able to detect the true bundle ID, user agent, and other properties of a generated impression using our patented, patent pending and trade secret IVT detection technologies, even when these characteristics may be declared as something else in the bidstream. When Pixalate detects mismatches in this data, the resulting impression is flagged as IVT.
Pixalate holds MRC Accreditation for Sophisticated Invalid Traffic (SIVT) detection and filtration across desktop, mobile web, mobile in-app, and connected TV (CTV) environments, including across (12) distinct server-side-ad-insertion (SSAI) measurement metrics.
How much money is lost to CTV app spoofing?
Pixalate estimates that in 2022 advertisers will lose over $38 million in the mobile open programmatic marketplace as a result of spoofed Apple iOS and Google Android apps. Here are the variables we used to arrived at this estimate:
- Emarketer projects 2022 Ad spend to be 123B on digital display ads.
- Social ad spend is estimated to be 56B (source), and CTV 8B (source)
- About 85% of the remaining ad spend is on mobile (desktop covering the rest) (source)
- About 10% of mobile is web traffic (source)
- And 11% of the traffic is open programmatic via open exchanges (as opposed to private marketplaces or closed channels) (source)
- Mobile app spoofing rate for apparent Apple iOS and Google Android apps was 0.78% in September/October 2022, according to Pixalate.
Where can I find more information about spoofed app traffic and other IVT concerns?
Pixalate’s Media Ratings Terminal (MRT) enables users to quickly check the breakdown of an app’s detected bundle IDs across Pixalate’s global pool of mobile data. For example, we see many instances of devices declaring in the bidstream to be associated with the bundle ID for Bally Sports, but Pixalate detects the true bundle ID as originating from other apps. Our MRT for mobile apps allows you to distinguish between spoofed traffic for a misrepresented app (“AppSpoofing” SIVT Type) and other IVT types for the app when its traffic is not misrepresented.
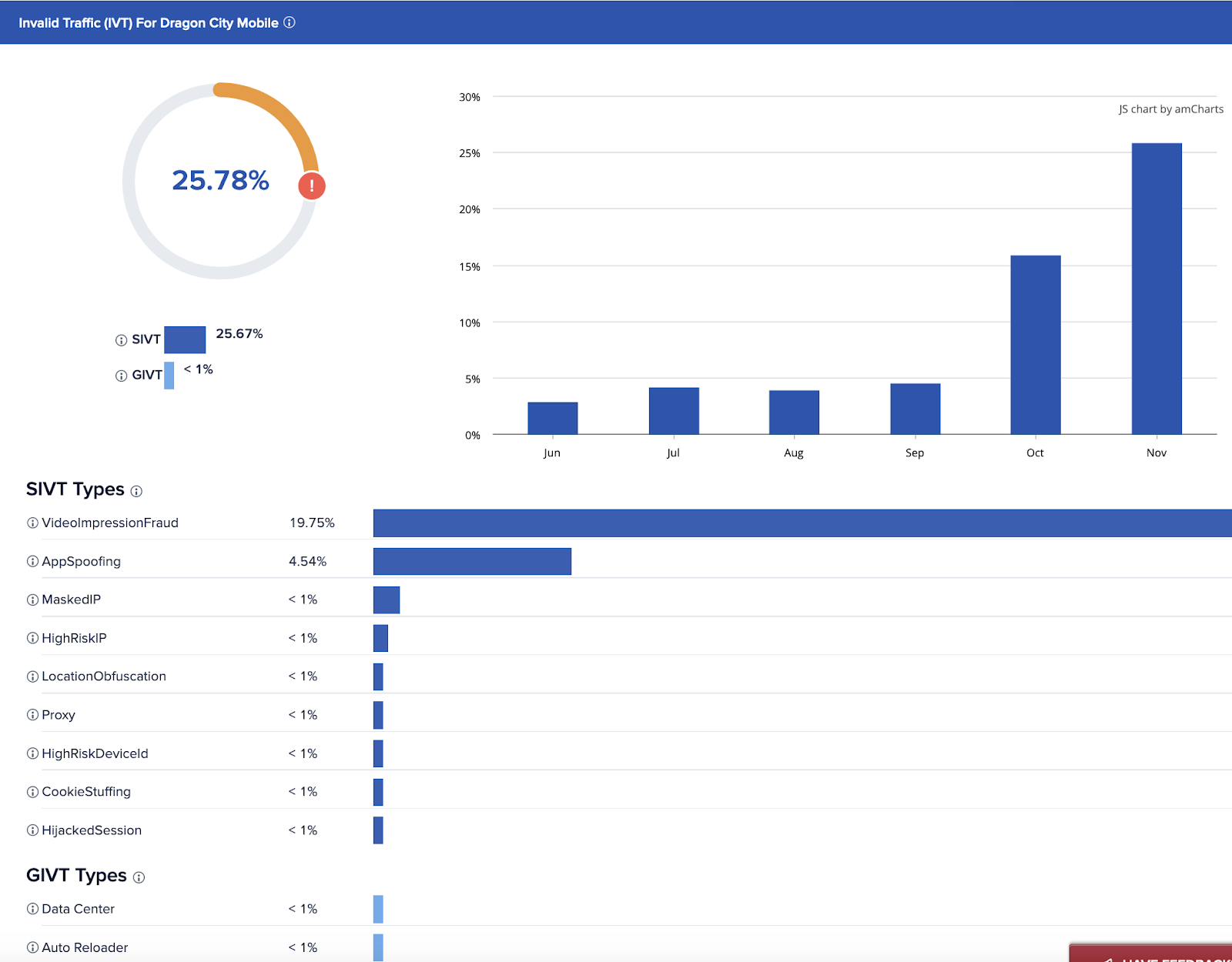
IVT details including App Spoofing for the “Dragon City Mobile” app (as seen in the MRT)
What was the criteria for the data in this report?
This Pixalate-generated report iOS and Android apps that have open programmatic advertising with an app spoofing rate (as measured by Pixalate) that meets a materiality threshold that we utilize. This technique allows us to focus on apps that appear to be significantly affected by app spoofing/misrepresentation in the global ecosystem. This filtered list is then sorted/ranked by the total number of flagged app spoofing impressions measured for each app.
How can I avoid app spoofing on mobile apps?
App spoofing can be mitigated by following certain best practices. For example, enforcing strict (not just a presence check) app-ads.txt and sellers.json validation to ensure that you are working with authorized sellers for the apps on which you are buying inventory. You may also use anti-fraud tools like Pixalate’s MRT and Analytics to better understand your potential exposure to app spoofing, and protect yourself accordingly.
For more information, please visit the Mobile App Spoofing article in our knowledge base.
Disclaimer
The content of this Ad Fraud Series Report reflects Pixalate’s opinions with respect to the factors that Pixalate believes may be useful to the digital media industry. Pixalate’s opinions are just that, opinions, which means that they are neither facts nor guarantees; and this Report is not intended to impugn the standing or reputation of any entity, person or app, but instead, to report findings and apparent trends pertaining to apps in the Apple App and Google Play mobile stores. Per the MRC, “‘Fraud’ is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes.” Also per the MRC, “‘Invalid Traffic’ is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”








