Using Overlap Reports
The Pixalate Analytics dashboard contains a section for Data Feed Overlap Reports where they show our clients the effectiveness of the pre-bid lists that they are subscribed to, and troubleshoot any potential issues with implementation.
On the left navigation of the dashboard, we show you a menu item called “Data Feeds”.
If you click on this menu item, you will see reports for the following as the time this KB article was published:
- Data Center
- IPv6
- High Risk Mobile Apps
- High Risk CTV Apps
- High Risk Websites
- CTV Device ID
- Mobile DEFASE (delisted from the app store) Apps
- CTV DEFASE (delisted from the app store) Apps
- Made for Advertising Mobile Apps
- Made for Advertising CTV Apps
- Made for Advertising Websites
- User Agent
- Supply Path Optimization
- COPPA Compliance Feeds:
- Child Directed Mobile Apps
- Child Directed CTV Apps
- COPPA Compliance Risk for Mobile Apps
- COPPA Compliance Risk for Mobile Apps
- Malformed CTV App IDs
- Proxy Gateways
As more data feed types are introduced by the Pixalate team over time, we will have corresponding reports to complement and illustrate how effective those feeds are to blocking sources of traffic quality issues.

These reports have two main objectives.
- Give a visual overview of when Pixalate uploads new lists to a secure FTP for download and consumption, and when the list is then downloaded by you, the client.
- This allows you to see if you are missing any lists or if there are any large gaps of time between when the list is uploaded and when you download it.
- Missing lists or having large gaps between consumption of lists and when they are made available can cause some leakage wherein bad IP’s, Device ID’s, user agents, apps or domains may end up in your traffic.
- Show our clients how effective the lists are at different probability thresholds. As you may be aware, Pixalate SIVT lists have probabilities associated with different data points. This is based on back-end analysis which gives us an overview of how “risky” an IP, Device ID, etc might be to transact on. Our probabilities range from .5 to 1, with 1 being deterministic that a given data point is a risk.
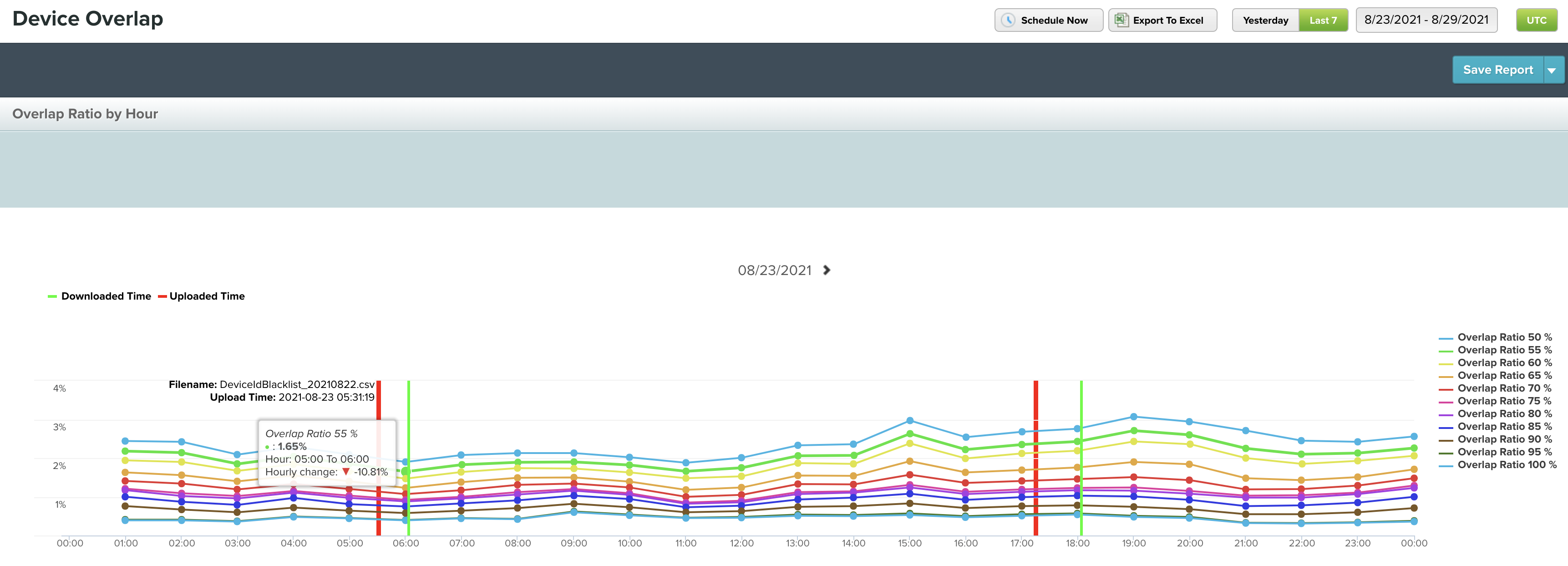


The reports give a seven day window showing how much ‘leakage’ there was in your traffic at a .5, .75 and 1 probability threshold. This allows us to see if the probability should be updated or changed, and if the expectations with applying the list(s) matches the data.
The Datacenter User Agent and Defased pre-bid lists are deterministic GIVT lists, with no probabilities. Therefore, the overlap report shows you whether the list is being applied properly. If it is being applied properly, there should be no leakage of data through your data.


MFA Domains overlap is based on the amount of traffic that has passed through and is designated with a medium or high categorization. For more on Pixalate's MFA methodology, please see here.

Overlap for the following lists will be based on mapping the passed bundle/app ID to the associated store ID. This is important to note as it will influence how the lists will be implemented for blocking purposes.
- Made for Advertising CTV Apps
- Child Directed Apps (CTV)
- High COPPA Compliance Risk Apps (CTV)
-1.png?width=150&height=60&name=pixalate-full-logo%20(1)-1.png)